- 2 Minutes to read
- Print
- DarkLight
- PDF
Single Sign-On (SSO)
- 2 Minutes to read
- Print
- DarkLight
- PDF
Stackify follows the Security Assertion Markup Language 2.0 (SAML 2.0) protocol for integration with external Identity Providers. Before attempting to configure this feature, please note the following:
- The SAML assertion
Subject > NameIdelement must have an email address in the SAML OASIS Email Format specification. - That email address must match a registered user in Stackify with that email address.
- Retrace's SSO configuration currently only works for idP initiated requests, so you will need to login through your SSO provider.
Getting Started
To keep things simple, we have provided a client user interface allowing a client to setup their own Single Sign-on (SSO) configuration. To access these settings open the menu item Settings and navigate to SSO under the Integrations section. The user must be authorized to manage users and roles in order to see this section. Users may choose to "Add Identity Provider" (IdP) or Edit an existing.

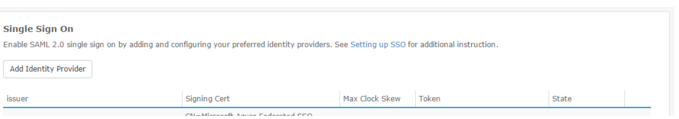
Adding an Identity Provider
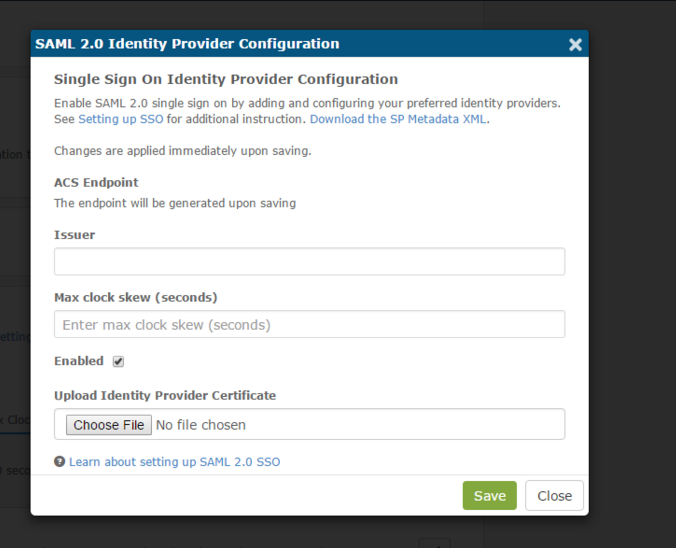
When adding a new identity provider, the user must provide just an Issuer name and the Identity Provider's public key certificate used to sign the response and/or assertion(s).
The Stackify SSO identity provider configuration allows for a client to adjust the max clock skew setting which is used to tune in expiration validation in case server times between the Identity Provider (IdP) or Service Provider (SP) are out of sync.

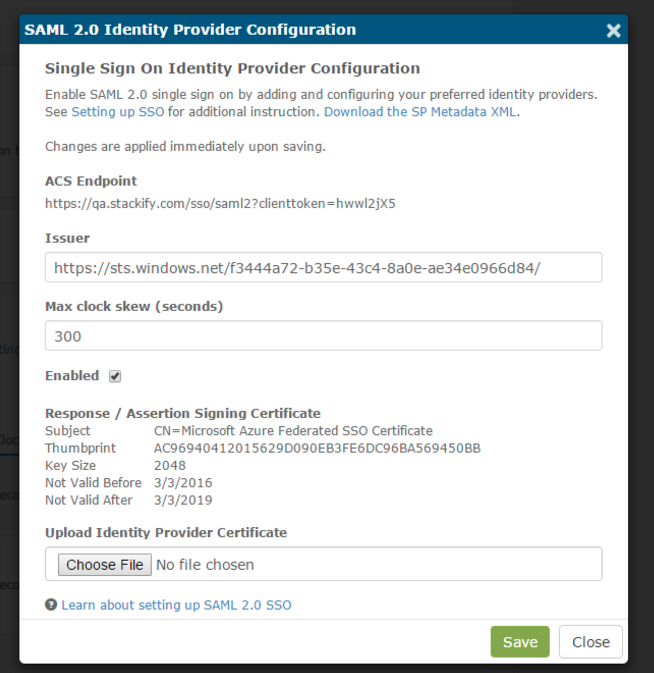
Fully-Configured SSO Provider
Upon saving or editing an Identity Provider, the user will be provided the ACS Endpoint which contains the Retrace generated client token. In addition, the dialog will update to present the public key certificate information which we will now use to validate signed SAML responses and signed assertions. Here's what a fully-configured SSO modal looks like when set up properly:

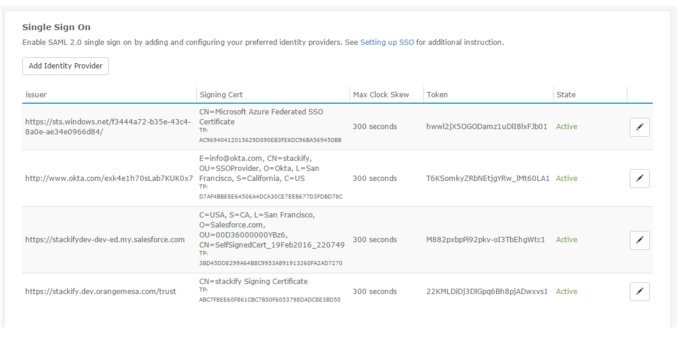
Authorized SSO Providers
After successfully authorizing any number of SSO providers in your Retrace account, you'll be able to see the provider details at the bottom of the page. The right columns on of the table will let you know if the provider is active, and also let you edit the providers credentials.
Encrypting the SAML Assertion (Optional)
Stackify will supply the client with a public key certificate which we recommend is used to encrypt the assertions within a SAML response; however, this encryption is not required. You can download the Service Provider's metadata XML file via the Download the SP Metadata XML link in the SAML 2.0 Identity Provider Configuration modal.
Account-Wide Enforcement (Optional)
Once you have configured an SSO identity provider, the option to enforce single sign-on for all users becomes available on the Account Information screen. Enabling this option disables local login for all user accounts. Any user logging in will be redirected to the configured identity provider for authentication. Only users who can configure account settings can enable this option.
To enable the enforce SSO option, navigate to the Account Information screen (Settings >> Account Settings) and locate the Security section. Check the box next to the Enforce Single Sign-On option to enable, uncheck to disable. Remember to Save Changes when finished.
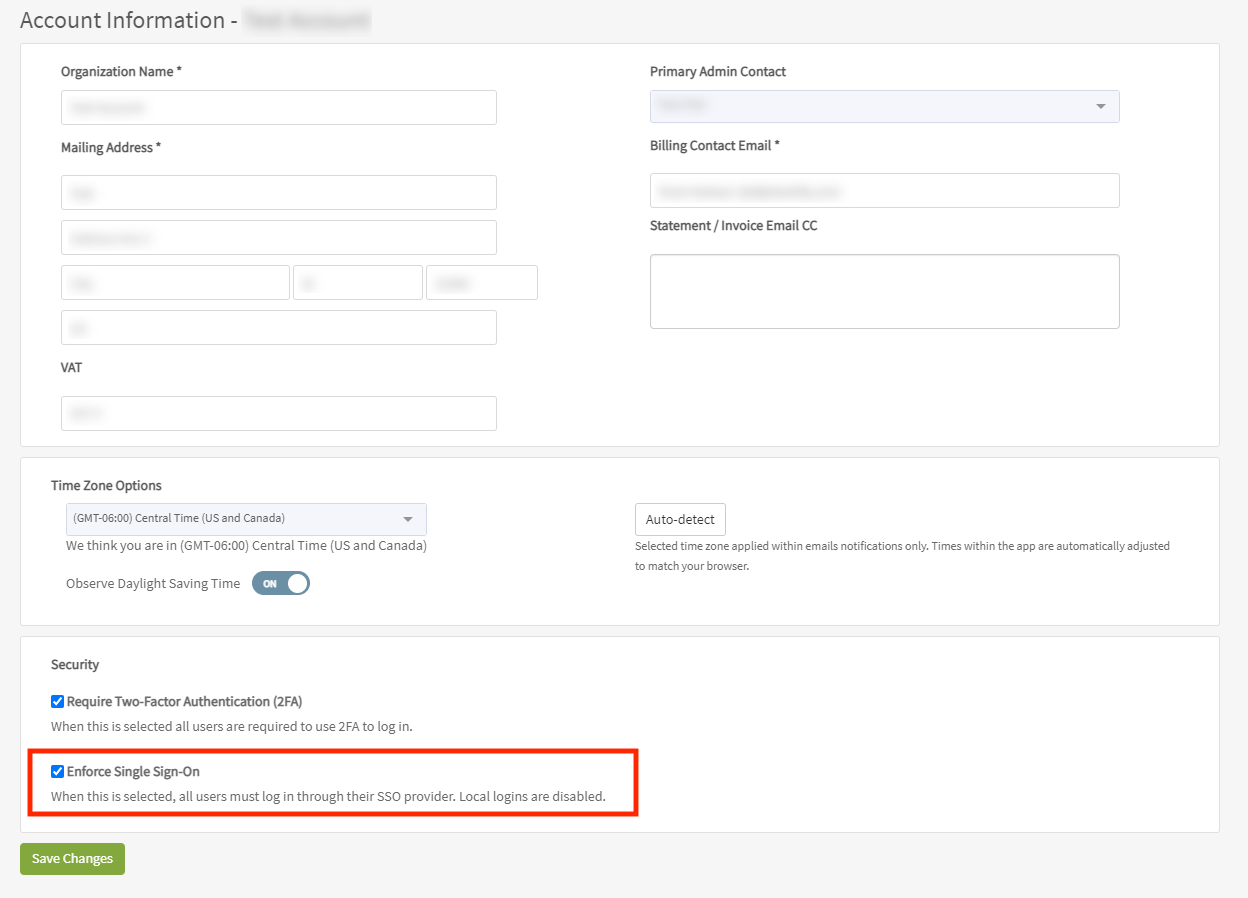
If the Enforce Single Sign-On option is unavailable (grayed out), an SSO identity provider has not yet been configured. Please configure a provider as indicated above.
Need Assistance?
If you need help setting up Single Sign-on functionality or have feedback about it, please don't hesitate to contact the support team: support@stackify.com.

